6.3.1.6. HOTP Token¶
The HOTP token is - together with the TOTP - the most common token. The HOTP Algorithm is defined in RFC4225. The HOTP token is an event base token. The HOTP algorithm offers two parameters: * The length of the generated OTP Value (6 or 8 digits) * The hashing algorithm to use (SHA1, SHA256 or SHA512).
The HOTP token implements the authenticate mode. With a suitable challenge_response policy, it may also be used in the challenge mode.
6.3.1.6.1. Hardware tokens¶
There are many token vendors out there who are using the official algorithm to build and sell hardware tokens. You can get HOTP based hardware tokens in different form factors, as a normal key fob for your key ring or as a display card for your purse.
6.3.1.6.1.1. Preseeded or Seedable¶
Usually the hardware tokens like keyfobs or display cards contain a secret key that was generated and implanted at the vendors factory. The vendor ships the tokens and a seed file.
Warning
In this case privacyIDEA can not guarantee that the secret seed of the token is unique and if you are using a real strong factor.
privacyIDEA also supports the following seedable HOTP tokens:
SafeNet eToken NG OTP
SafeNet eToken Pass
Yubikey in OATH mode (See Yubikey Enrollment Tools on how to enroll Yubikeys in HOTP mode.)
Daplug
Those tokens can be initialized by privacyIDEA. Thus you can be sure, that only you are in possession of the secret seed.
6.3.1.6.1.2. Experiences¶
The above mentioned hardware tokens are known to play well with privacyIDEA. In theory all OATH/HOTP tokens should work well with privacyIDEA. However, there are good experiences with Smartdisplayer OTP cards 1 and Feitian C200 2 tokens.
6.3.1.6.2. Software tokens¶
Besides the hardware tokens there are also software tokens, implemented as Apps for your smartphone. These software tokens allow are seedable, so there is no vendor, knowing the secret seed of your OTP tokens.
But software tokens are software after all on device prone to security issues.
6.3.1.6.2.1. Experiences¶
The Google Authenticator can be enrolled easily in HOTP mode using the QR-Code enrollment Feature.
The Google Authenticator is available for iOS, Android and Blackberry devices.
6.3.1.6.3. Enrollment¶
Default settings for HOTP tokens can be configured at HOTP Token Config.
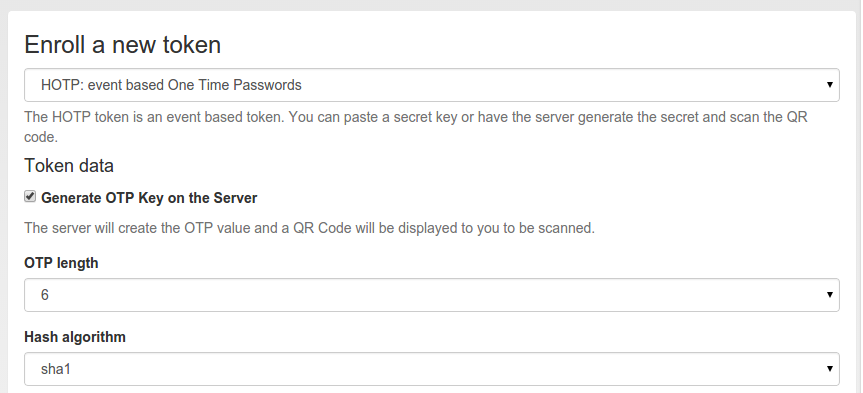
Enroll an HOTP token¶
During enrollment you can choose, if the server should generate the key or if you have a key, that you can enter into the enrollment page.
As mentioned earlier, you can also choose the OTP length and the hash algoriothm.
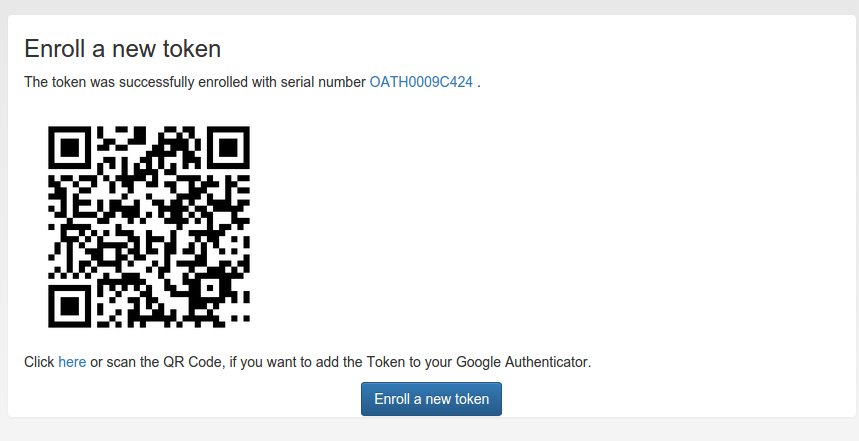
If the server generated the secret seed, you can scan the QR-Code¶
After enrolling the token, the QR-Code, containing the secret seed, is displayed, so that you can scan this with your smartphone and import it to your app.
